Vulnerability Assessment Services
Talk to us now!

Partner with Aress to evaluate threats and vulnerabilities in your existing industrial cybersecurity program. We offer complete vulnerability assessment services to protect from attacks or malicious software.
Is your company’s IT system vulnerable to attacks by malicious outsiders? Are you looking for a professional team for vulnerability scanning and protecting? Our Vulnerability Assessment Services are aimed to assist an organization in minimizing risks that may pose threat to the organization’s IT infrastructure. Through the assessments, we provide a way of improving the security levels and minimizing cyber threats that you are facing.
Expertise and Experience: Our team consists of certified security professionals with proper knowledge in the analysis of weaknesses in several businesses. We keep ourselves updated with the latest security threats and security trends to offer effective solutions.
We understand that no two organizations are alike, hence the vulnerability assessments that we provide are scalable to the particular infrastructure and IT environment of your company, compliance needs, and business goals and objectives.

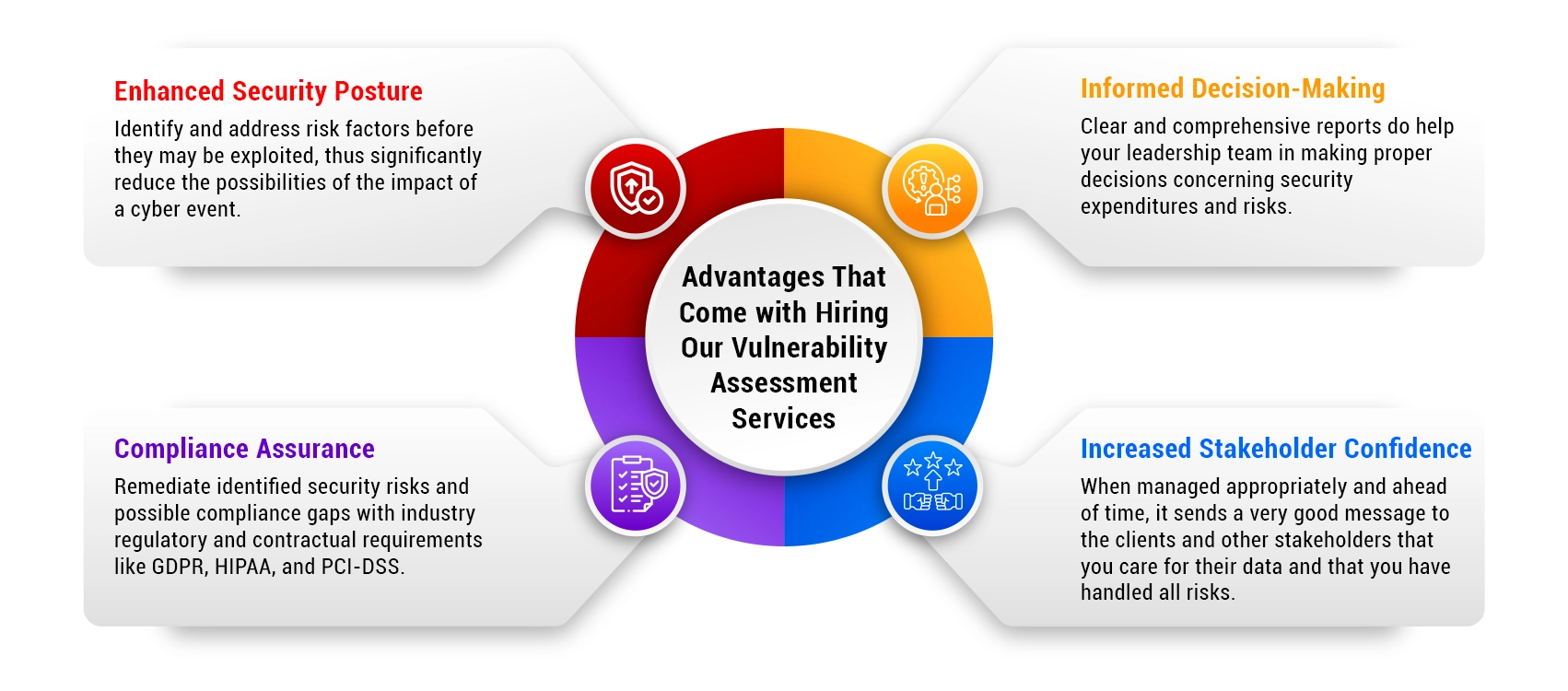
Our assessments do not only focus on the recognition of weaknesses. We offer our clients risk reports that focus on the likelihood, the business impact, and ease of exploitation. This means that you get to attend to all the critical issues first, which is absolutely essential.
We offer ongoing support service as we help you remediate vulnerabilities and improve your overall security posture. Our team is available to help you in carrying out the recommendations and subsequent evaluations.
Our vulnerability assessment services follow a structured approach to provide clear guidelines for the evaluation and proper treatment of investigating vulnerabilities.
It starts with identifying how your organization works, its goals, and the security threats by holding a meeting with the client. This makes it possible for us to come up with specific methods of evaluating your business according to your needs.
Collectively we decide on the sampling of the assessment this involves deciding on the systems, applications, and networks to be sampled. This step helps us to concentrate on the most important elements of your infrastructure only.
Credible and real-time tools and techniques are used to perform scans from where vulnerabilities are identified in your environment.
This includes:
For further assurance, our team of professionals does the scanning manually so as to be in a position to detect other vulnerabilities that the automated scanners may perhaps miss. Manual means are applied by our specialists to check information and look for possible threats that the software tools can overlook.
This includes:
We identify the impact of the particular vulnerability and the likelihood of its occurrence. We prioritize vulnerabilities based on factors such as:
We deliver a detailed report that outlines our findings, including:
This report becomes your roadmap to guide you in your vulnerability management efforts.
Our team offers recommendations on how we can deal with the identified vulnerabilities. Some of the support services may include technical support to your company, and policy advisory where we help in developing policies on security.
This means that the vulnerability management is continuous. We offer you periodic assessments and also ongoing scanning services to protect against new threats.
Contact us for more details. We are happy to help you in all cloud support related questions.