Web Application VAPT
Talk to us now!

Web application penetration testing is a security practice where simulated cyber-attacks are performed on a web application to identify and exploit vulnerabilities. The goal is to determine the security posture of the web application by performing attacks using sophisticated techniques.
This type of testing helps organizations understand the effectiveness of their security measures and identify areas that need improvement to protect against real-world threats. It’s a crucial part of maintaining robust cybersecurity defenses for any web-based application.
There are multiple benefits of getting Web Application VAPT done for your Web Applications. Some of the most important are listed below.

Early Identifying of vulnerabilities allows organizations to identify and address security threats before they escalate into significant breaches.
It safeguards user data from potential breaches and unauthorized access.

It ensures adherence to data protection regulations and industry standards.

Identifying & fixing vulnerabilities improves the security posture of a web application.

By identifying and fixing vulnerabilities, it maintains a positive brand image and user trust.

Ensures users that their sensitive information is secure, enhancing user confidence and loyalty.
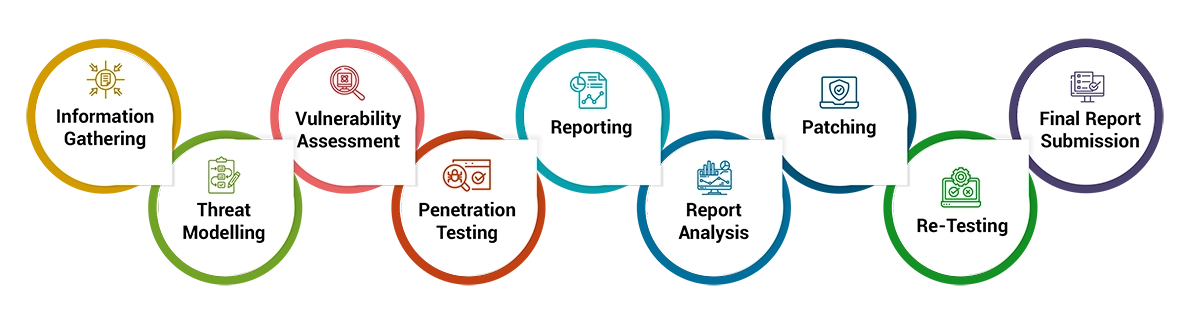
Understand the web application testing scope, functionalities, architecture and procure the necesary data like test login credentials, etc.
Identify potential attack vectors and scenarios specific to the web application.
Employ automated scanning tools and manual analysis techniques to identify vulnerabilities in the web application.
Simulate real-world attacks attempting to exploit vulnerabilities to understand their impacts and potential risks.
Provide a detailed report outlining identified vulnerabilities, their impacts along with the necessary remediation steps to be taken.
Development teams to address vulnerabilities based on the provided recommendations to improve the web application security posture.
Conduct a VAPT re-evaluation to ensure that vulnerabilities have been effectively addressed.
Deliver a final comprehensive report detailing the assessment findings & actions taken.








Contact us for more details. We are happy to help you in all cloud support related questions.