Network VAPT
Talk to us now!
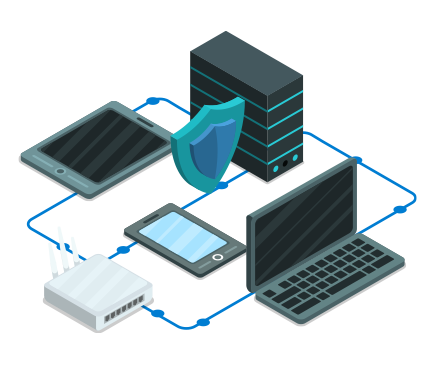
Network Vulnerability Assessment and Penetration Testing (VAPT) is a comprehensive cybersecurity exercise aimed at identifying, exploiting and addressing vulnerabilities within a network infrastructure. It involves a systematic review of network systems, applications, and devices to discover potential security weaknesses that could be exploited by cyber threats.
As a part of this process, trained cybersecurity professionals use a combination of automated tools & manual techniques to simulate real-world attacks on the network. This includes scanning for known vulnerabilities using automated tools, analyzing configurations, and attempting to exploit weaknesses to evaluate the effectiveness of security measures implemented.
The objective of Network VAPT is to proactively identify and remediate vulnerabilities to enhance the overall security posture of the network and minimize the risk of unauthorized access, data breaches, and other cyber threats. By conducting regular VAPT assessments, organizations can stay ahead of potential security risks and ensure the robustness of their network defenses.
There are multiple benefits of getting VAPT done for networks. Some of the most important are listed below.

Proactively identifying and fixing vulnerabilities to prevent exploitation by malicious actors.

Enhancing the resilience of network systems to ensure uninterrupted business operations.
It safeguards user data from potential breaches and unauthorized access.
Identifying vulnerabilities in the network infrastructure, including software, hardware, and configurations.
Meeting regulatory requirements and industry standards by regularly testing and securing the network.

Minimizing the risk of financial losses associated with data breaches, downtime, and regulatory fines.
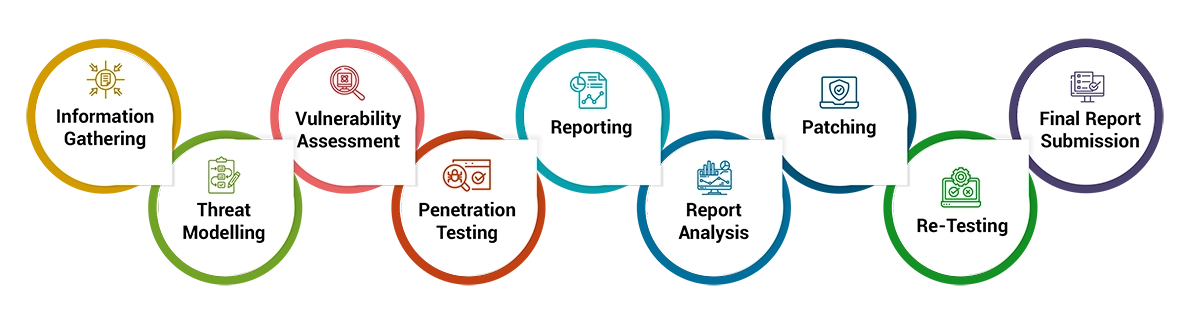
Defining the scope of the assessment, specifying the systems and networks to be tested.
Gather information about the target network including domain names, IP addresses, etc.
Utilize automated tools to scan to scan the network for known vulnerabilities, misconfigurations, and weak points.
Simulate real-world attacks attempting to exploit vulnerabilities to understand their impacts and potential risks.
Provide a detailed report outlining identified vulnerabilities, their impacts along with the necessary remediation steps to be taken.
Development teams to address vulnerabilities based on the provided recommendations to improve the network security posture.
Conduct a VAPT re-evaluation to ensure that vulnerabilities have been effectively addressed.
Deliver a final comprehensive report detailing the assessment findings & actions taken.






Contact us for more details. We are happy to help you in all cloud support related questions.