IoT Devices Security
Talk to us now!

The Internet of Things (IoT) is the system of physical objects - devices, vehicles, homes and different things embedded with electronics, software, sensors, and network connectivity—that empowers these objects to gather and interact data.
IoT Security testing is a process of testing IoT devices to find security vulnerabilities that hackers could exploit to access your network, modify your data, or steal your information.
If IoT devices are not secured, any connected object from smart watches to manufacturing bots, can be hacked. Once hackers gain control, they can use this levarage and steal the user's digital data.
There are multiple reasons of getting security testing done for IoT devices. Some of the most important are listed below.

Proactively addresses vulnerabilities to prevent cyber threats.
Safeguards sensitive data from breaches and unauthorized access.

Maintains positive brand image and user trust by identifying vulnerabilities.

Ensures adherence to data protection regulations and standards.

Demonstrates commitment to security, giving a competitive advantage.
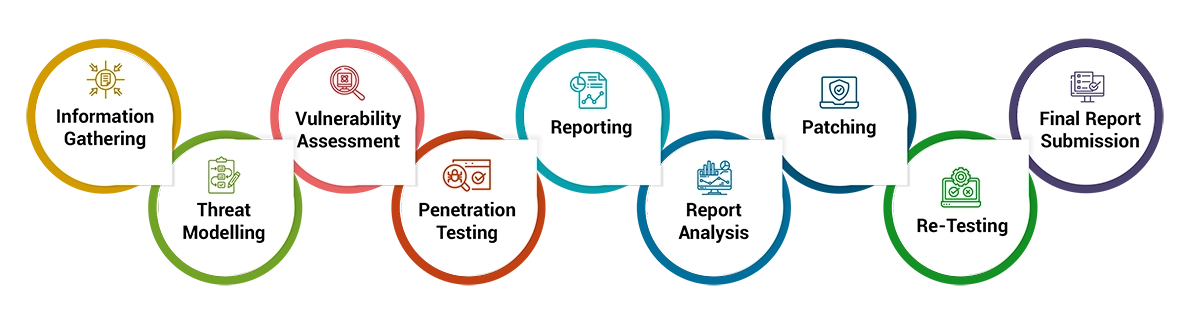
Clearly define the boundaries of the assessment, specifying which IoT devices, networks, and applications will be tested.
Gather essential information about the IoT environment, including device specifications and network architecture, to understand potential vulnerabilities and attack vectors.
Identify potential attack vectors and threats that could affect the IoT device and prioritize them based on their impact on device functionality and data security.
Utilize automated tools & manual techniques to scan IoT devices hardware, Firmware & radio connectivity for known vulnerabilities, misconfigurations, and weak points that could be exploited by attackers.
Conduct controlled penetration tests on the IoT device to simulate real-world attacks and exploit identified vulnerabilities to assess the effectiveness of security controls.
Provide a detailed report outlining identified vulnerabilities, their impacts along with the necessary remediation steps to be taken.
Development teams to address vulnerabilities based on the provided recommendations to improve the IoT device security posture.
Conduct a VAPT re-evaluation to ensure that vulnerabilities have been effectively addressed.
Deliver a final comprehensive report detailing the assessment findings & actions taken.




Contact us for more details. We are happy to help you in all cloud support related questions.