DevSecOps Consultation & Implementation
Talk to us now!

DevSecOps is the practice of integrating security into a continuous integration, continuous delivery, and continuous deployment pipeline. DevSecOps is the practice of integrating security practices at every stage of the software development process. It includes tools and processes that encourage collaboration between developers, security specialists, and operation teams to build software that is both efficient and secure.
The primary objective of implementing DevSecOps is to have security controls through the entire software development lifecycle, as against the traditional approach where security assessments are done at the end of the software development lifecycle.
DevSecOps helps software teams detect security issues at earlier stages and reduce the cost and time of fixing vulnerabilities.
DevSecOps stands for development, security, and operations. It is an extension of the DevOps practice.
Each term defines different roles and responsibilities of software teams when they are building software applications.

Development is the process of planning, coding, building, and testing the application.

Security means introducing security earlier in the software development cycle. For example, programmers ensure that the code is free of security vulnerabilities, and security practitioners test the software further before the company releases it.

The operations team releases, monitors, and fixes any issues that arise from the software.
The primary goals and benefits of DevSecOps are those that open the door for organizations to experience advancement in operational efficiency across various departments. This includes:
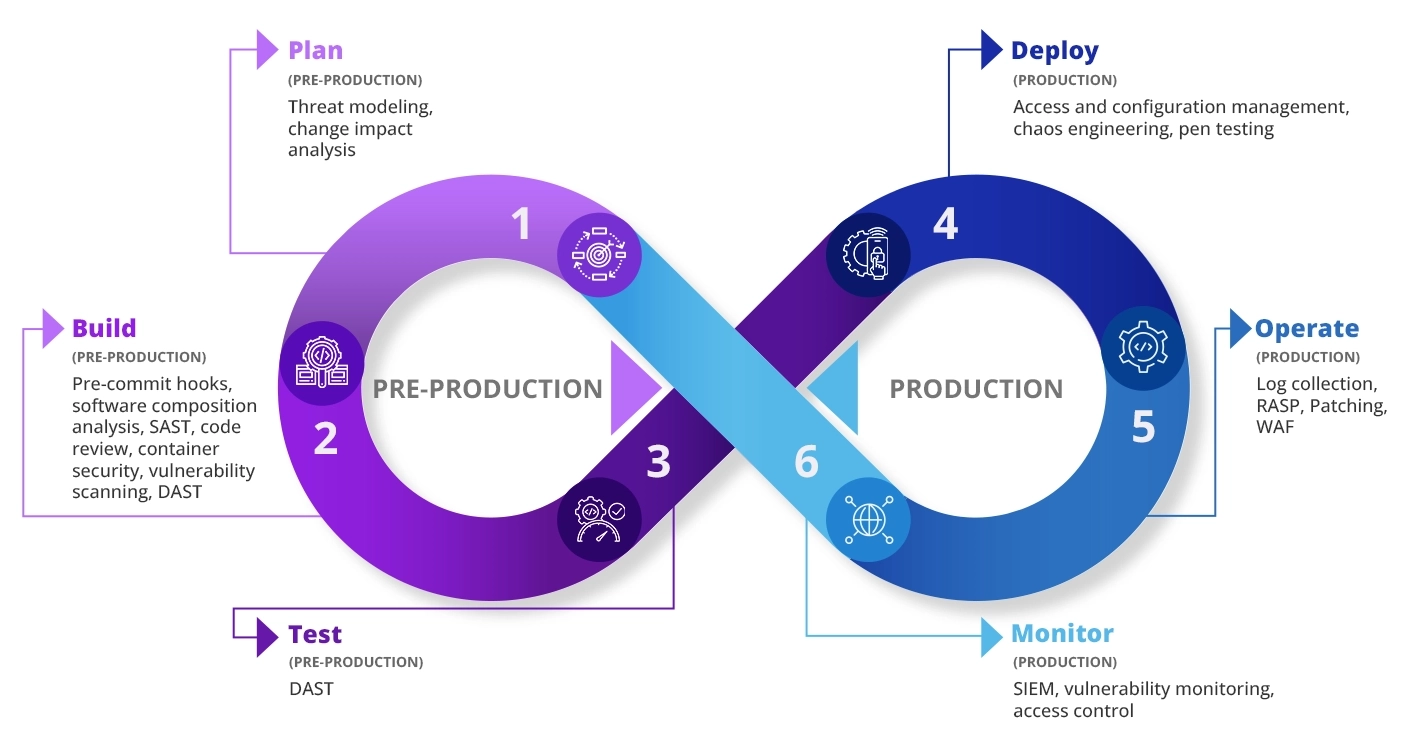
The plan phase involves collaboration, discussion, review, and strategy of security analysis. Threat Modelling using different models like STRIDE & DREAD is performed as a part of this phase.
Security scanning tools are integrated in the Integrated Development Environment (IDE) as a part of this phase, so that developers can scan for security issues immediately after they write some code in the IDE.
The build phase begins once developers commit code to the source repository. DevSecOps scanning tools are integrated in the CI/CD pipeline and are targeted to peform automated scanning on the build artifact. Security scans such as Software Composition Analysis (SCA) scans and Static Application Software Testing (SAST) are performed as a part of this phase.
Automated scanning tools such as Veracode are used to perform scanning in this phase.
The test phase is triggered after the UI and backend code is properly integrated in staging or testing environments.
The test phase uses dynamic application security testing (DAST) tools to detect live application flows like user authentication, authorization, SQL injection, and API-related endpoints. The security-focused DAST analyzes an application against a list of known high-severity issues, such as those listed in the OWASP Top 10.
Tools like Burp suite & OWASP Zap can be used to perform DAST scans in this phase.
If the earlier process goes well, it’s the proper time to deploy the build artifact to the production phase. The security problems affecting the live production system should be addressed during deployment. For instance, it is essential to carefully examine any configuration variations between the current production environment and the initial staging and development settings. In addition, production TLS and DRM certificates should be checked over and validated in preparation for upcoming renewal.
Organizations can also apply chaos engineering principles by testing a system to increase their confidence in its resilience to turbulence. Replicating real-world occurrences such as hard disc crashes, network connection loss, and server crashes is possible.
Another critical phase is operation, and operations personnel frequently do periodic maintenance. For eg: Operation teams should monitor Zero-day vulnerabilities and monitor them frequently.
Once an application is deployed and stabilized in a live production environment, additional security measures are required. Companies need to monitor and observe the live application for any attacks or leaks with automated security checks and security monitoring loops.
SIEM tools can be implemented at this stage. Another security technique is to offer a bug bounty program that pays external individuals who report security exploits and vulnerabilities.
Contact us for more details. We are happy to help you in all cloud support related questions.