API Security
Talk to us now!
API VAPT, or Application Programming Interface Vulnerability Assessment and Penetration Testing, is a critical cybersecurity practice designed to ensure the security of your API calls.
When an organization uses an API, it exposes itself to cyber attacks because if APIs are not secure, then they can be compromised easily. A successful attack can result in data theft or even complete destruction of the system or network. Therefore, it is important for organizations to test their APIs regularly and make sure they are not vulnerable to attacks that could lead to data loss and other problems.
There are multiple benefits of getting VAPT done for APIs. Some of the most important are listed below.
It safeguards user data from potential breaches and unauthorized access.

Vulnerabilities like “No rate limit” if exploited can result in huge costs to an organization.

Secure APIs ensure your applications function smoothly without disruptions.

Secure APIs build trust with customers, preserving your business's reputation.

API security can help you gain a strategic advantage in the digital world, as customers and partners increasingly demand secure interfaces.

We can proactively identify vulnerabilities, reducing the risk of cyberattacks.
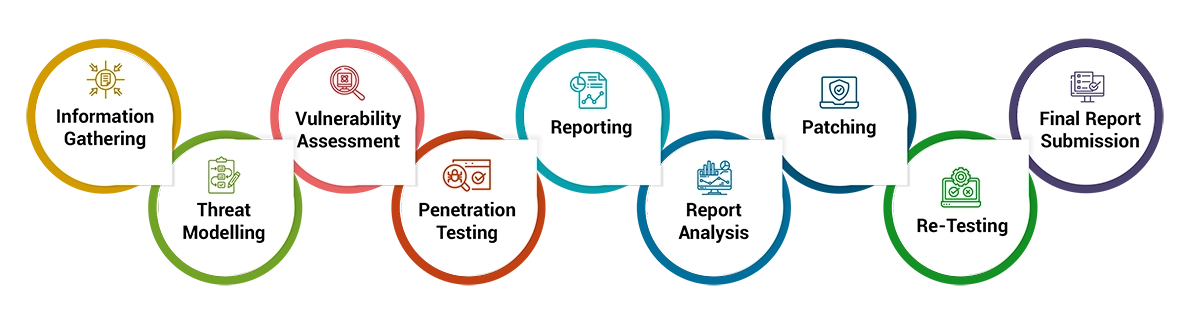
API security testing is a process of carefully evaluating API endpoints to identify and remediate vulnerabilities such as fuzzy input, parameter tampering or injection attacks. Acting as the first line of defense, it meticulously examines endpoints to identify and neutralize vulnerabilities before attackers can exploit them.
Define the scope of the assessment, including which APIs will be tested, the testing environment, and specific objectives.
Gather information about the APIs, such as endpoints, protocols, and communication methods.
Identify potential attack vectors and threats and vulnerabilities that could affect the APIs and their users.
Utilize automated tools to scan for common vulnerabilities, including injection, authentication, and authorization issues.
Perform manual testing to identify vulnerabilities that automated tools may miss, such as logical flaws and business logic issues.
Simulate real-world attacks attempting to exploit vulnerabilities to understand their impacts and potential risks.
Provide a detailed report outlining identified vulnerabilities, their impacts along with the necessary remediation steps to be taken.
Development teams to address vulnerabilities based on the provided recommendations to improve the API security posture.
Conduct a VAPT re-evaluation to ensure that vulnerabilities have been effectively addressed.
Deliver a final comprehensive report detailing the assessment findings & actions taken.




Contact us for more details. We are happy to help you in all cloud support related questions.